Lookout Security identified a new Android Trojan, LeNa, which is said to be an evolution of the Legacy variant discovered earlier this year (also known as DroidKungFu). While previous Legacy variants were spotted only in alternative app markets and forums in China, this one (called LeNa) has also been caught on the Android Market (though the affected apps have been deleted by Google in the meantime).
Here’s how it works (from Lookout’s press release):
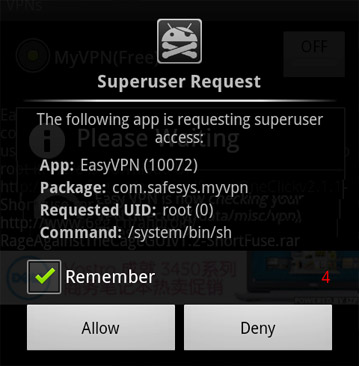
Unlike its predecessors, LeNa does not come with an exploit to root the device, rather it requests privileged access on a pre-rooted device. On un-rooted devices, it offers “helpful” instructions on how to root the phone. In some samples, LeNa is re-packaged into apps (a VPN management tool, for instance) that could conceivably require root privileges to function properly. Other samples attempt to convince the user that root access is required to update. Once the user grants LeNa with root privileges, it starts its infection process in the background, while performing the advertised application tasks in the foreground.
Once on a user’s device, the Trojan takes a different tactic than previously seen to infect and launch the malware. LeNa hides itself inside an application that is native to the device (an ELF Binary). This is the first time an Android Trojan has relied fully on a native ELF binary as opposed to a typical VM-based Android application. In essence LeNa trojanizes the phone’s system processes, latching itself onto an application that is native to the device and critical to making the phone function properly.
So how to stay safe? Use common sense – install apps only from trusted sources, check the permissions an app requests, be alert for unusual behavior on your phone, and (optionally) download a mobile security app. And in case you care, you can get the complete technical teardown on LeNa from here.